
Preview image mashup credit: Email Self Defense – the Free Software Foundation.
This is a continuing episode in my tutorial series on email privacy and security. Earlier episodes detail a variety of ways to encrypt and secure your email. This episode will talk about how we as technologists can rebuild email for the digital age.
The importance of email privacy hit home for me recently as I emailed friends about my brain tumor diagnosis. There was no easy way to get the word out without sharing a very personal note with mail servers for Gmail, Hotmail, Yahoo, Comcast and Apple (.me). Any semblance of privacy at that point was purely illusory. Most of the emails I exchanged with healthcare providers over the following weeks would also be highly insecure.
Rather than discuss how email can be improved to enhance security, I declare it’s fundamentally broken in ways that we need to overhaul for the modern digital communications age.
In this tutorial, I’ll describe how email’s broken and talk about principles of Apple Pay, the company’s new mobile payment system, that could be applied to build a modern messaging infrastructure that offers end-to-end security. Not all of Apple Pay’s inspiration is technical; some of its greatest strength lies in shifting the emphasis away from corporate profit and data gathering and towards benefitting consumers with faster, more secure, more private transactions.
Keep in mind, I do participate in the discussions below. If you have a question or topic suggestion, please post a comment below. You can also message me on Twitter @reifman or email directly.
What’s Broken About Email Privacy and Security
Email privacy and security are fundamentally broken. The vast majority of emails we send float around the Internet unencrypted as plain text.
In One Does Not Simply Send An Email, journalist Quinn Norton writes:
[Email] has no network security designed into it at all. Partly this is because what we use for email was meant to be a temporary measure, a stopgap while the real protocol was developed. That was 1982. It got a small update in 2008, but email remains profoundly insecure.
Most free webmail service providers like Google think of its users as products not people. Gmail is free, so it can learn as much about us as it can for its advertising business.
If you use a common mail host like Google’s, all of your email is accessible to it, its internal analysis engines, and any government with illegal or court-approved access. Outbound emails you’ve sent to people at other mail hosts can be relatively easily recovered through similar surveillance or access.
Your IP address is logged as you access and send messages, providing a partial trail of your physical location (if that’s not already recorded by your cellphone’s service providers).
In fact, just accessing and sending emails with your phone opens up additional attack vectors: your cell phone company, backup provider such as iCloud, or forced surveillance in customs during a border stop. For example, earlier this year, a T-Mobile representative called me to respond to Un-truthful Carrier: Ten Lies T-Mobile Told Me About My Data Plan and startled me as he casually rattled off the common domains I was accessing data from on my phone.
Given these weaknesses, anything you write in an email likely is discoverable forever. And there’s no way of knowing if, when, how and by whom your email’s been accessed.
Furthermore, messages can be altered and faked by impostors (such as with a man in the middle attack). Email can be used to subject you to phishing attacks and deliver trojan horses. As Norton says, “Email is a dangerous thing.”
What About Encryption?
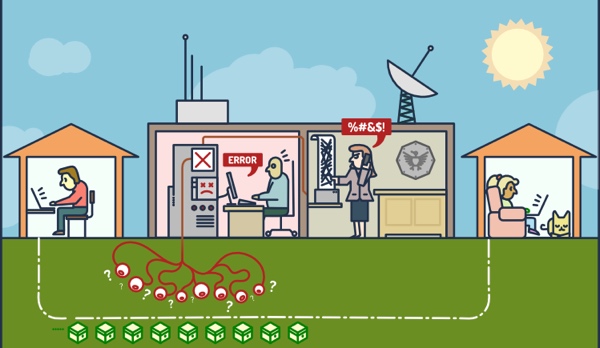
Image credit Email Self Defense – the Free Software Foundation
Public key encryption remains quite difficult to set up and use. Even if you’re able to, most of the people you regularly email probably won’t be. If you’ve been reading my tutorials, you probably have realized this by now. It’s hard to get our friends to start using it and hard to use routinely.
Even when used properly, encryption does nothing to protect the identity of the people you’re emailing with unless they are using anonymous email addresses and logging in using a service such as TOR. Message envelopes remain open.
What Apple Pay Does Well
While Apple Pay is not a messaging system, it provides a conceptual inspiration for a more secure email system. Here are some of the things that it does well that we can learn from. You can read more in the Apple Pay Security and Privacy Overview.
- Your purchases are private between your credit card company and each individual merchant.
- Your card number and security code aren’t shared with anyone.
- Apple doesn’t collect any transaction information that can be tied back to you.
- Neither Apple nor your device sends your credit or debit card number. Before they approve the payment, your bank or payment network can verify your payment information by checking the dynamic security code to make sure it’s unique and that it’s tied to your device.
- All aspects of the transaction are encrypted and managed by Apple.
- The Secure Element is an industry-standard, certified chip designed to store your payment information safely. The Device Account Number in the Secure Element is unique to your device and to each card added. It’s isolated from iOS and Watch OS, never stored on Apple Pay servers, and never backed up to iCloud.
- You can suspend Apple Pay whenever you want to stop using it.
Apple took steps with Apple Pay to improve our lives, making shopping quicker, easier and private, without trying to maximize its profits. They challenged the status quo of the unscrupulous credit-card providers and did so with the consumer in mind. It represented a shift in the direction of the development of the kinds of services that make up the fabric of our everyday lives.
Apple Pay takes a balanced, long-term approach to redesigning and deploying payments, hinting at how a single provider can provide a secure service in the best interests of its customers.
A More Secure Email Architecture
If we apply some of the principles of Apple Pay to a privacy-oriented email system, it would offer similar features:
- The cloud store of your inbox would be encrypted and anonymized, indecipherable to prying eyes and governments.
- Messages in transit would be fully encrypted.
- Message envelopes between recipients would be encrypted.
- Mobile apps that store message data locally would also operate on encrypted data.
- The initial exchange of messages between parties would be performed in a way that protected their privacy.
- Account deletion is complete and verifiable.
Certainly, there are providers trying to move messaging in this direction.
Our earlier episodes guided you through using third-party add-ons to encrypt messages, such as GPG Tools, and Keybase, an emerging public directory of verifiable keys. And Whisper Systems’ Signal app provides encrypted messaging and calls.
Lavabit once offered a secure email system that provided a number of these features, but its founder shut it down rather than face the threat of complete government access. Silent Circle similarly did so as well.
But now the founders of these inspired privacy-oriented mail systems are back.
The Dark Mail Alliance
The Dark Mail Alliance consists of the founders of these two companies, Silent Circle and Lavabit, making an effort to build a secure, private email system which pushes the industry to support open standards that provide common privacy protections across the sector—many of which remind me of Apple Pay.

The Dark Mail Mission
To bring the world our unique end-to-end encrypted protocol and architecture that is the ‘next-generation’ of private and secure email. As founding partners of The Dark Mail Technical Alliance, both Silent Circle and Lavabit will work to bring other members into the alliance, assist them in implementing the new protocol and jointly work to proliferate the world’s first end-to-end encrypted ‘Email 3.0’ throughout the world’s email providers. Our goal is to open source the protocol and architecture and help others implement this new technology to address privacy concerns against surveillance and back door threats of any kind.
The team appears to be making solid progress. You can read its detailed Internet Mail Environment Architecture and Specifications (pdf) in which Levison dedicates his project to the National Security Agency:

And you can watch his DEF CON 22 presentation on Dark Mail:
Recently, ZDNet reported that the first Dark Mail providers are coming soon. Says Levison, “Because so much time has been dedicated to developing the dark mail protocols, someone else may have better luck taking the open-source code and getting the first dark mail email provider up and running.”
Apple Pay set a precedent that doing right by consumers is the right thing to do and hopefully will make it more likely that other companies will openly consider adopting Dark Mail support. For now, we watch and wait—without any routine email privacy.
Please feel free to post your questions and comments below. You can also reach me on Twitter @reifman or email me directly. You can find my other tutorials by browsing my Envato Tuts+ instructor page.