If you’re concerned with working securely or anonymously online, the chances are you’ll have used a VPN (Virtual Private Network) at some stage. But when choosing a VPN service do you know what factors you should be taking into account? This tutorial will help you understand why you should use a VPN and how to choose the right service for you.
Here Are the Topics We’ll Cover
- Internet Security and Privacy
- Who Can Access My Unsecured Information?
- A Simple, Real-World Example
- What is a VPN?
- What Are the Pros and Cons of Using a VPN?
- How to Find the Best VPN For Your Needs
Watch the Screencast
What Does Privacy and Security Mean?
We live in an age where online privacy, if you aren’t paying attention, is almost non-existent. Our online usage is tracked continuously, be it our browsing, our shopping habits, our social media, education, or our entertainment. And all that information helps build pictures of us as consumers–pictures which are often given or sold to companies for marketing purposes.
You might not think that having your internet usage, or the identity of your computer or device, passed on to third parties is a big deal, and you aren’t alone. But these details may only be the tip of the iceberg, and by making them publicly available you may also be opening up the door to other, more sensitive, information, such as login credentials:
- or your bank account
- for company accounts, such as email, or intranets.
- for a personal website, or social media
These details may all be up for grabs if you’re using them over an unencrypted or unprotected network.
Tip: besides secure networks, you should also consider using a password manager such as 1Password, and Two Factor Authentication to protect your login credentials.
Who Can Access My Unsecured Information?
So we’ve covered the fact that an insecure network can leave your sensitive information exposed, but who can actually get to it? Here’s a quick list:
- Your ISP (Internet Service Provider)
- Administrators of public WiFi networks (think coffee shops, airports, shopping malls etc.)
- Hackers
Deliberate hacking, often with malicious intent, is behind all of the highest-profile data breaches of recent memory.
- Yahoo! Was breached in 2014. Over 3 billion accounts were compromised causing an estimated $350M loss for the floundering web services provider, which at the time was negotiating an acquisition to Verizon.
- Between 2014 and 2018 Marriot International reported that roughly 500M customers had had their data stolen. This data included names, passport numbers, and even credit card details.
- The FriendFinder network mainly has websites with adult content, and reported in 2016 that almost 20 years’ worth of user data had been exposed.
These examples should demonstrate that data breaches are serious. The exposure of personal data can cause huge personal distress to those involved, and often has huge financial repercussions too. But these examples are all large-scale corporate controversies–how might we apply what we’ve learned to individuals?
A Simple, Real-World Example
Let’s imagine we have a WordPress developer, and that developer is responsible for managing a number of WordPress websites. He or she works largely from home, but sometimes works from a coffee shop, or an airport when travelling. Now, because our developer is logging into various WordPress websites over those unencrypted public networks, the login credentials are potentially vulnerable.
Someone with malicious intentions, who manages to intercept WordPress login details by sitting between our developer’s computer and the network’s endpoint, could wreak havoc on the client’s websites, go further and take advantage of other users’ details stored on those websites, and leave our developer personally liable.
One measure our developer could have put in place to protect those websites, is a VPN.
What is a VPN?
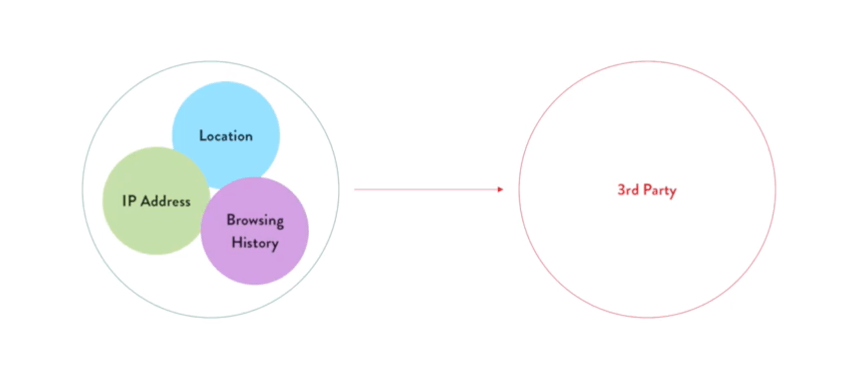
Think of a VPN, or Virtual Private Network, as an intermediary between you and your online destination. Without a VPN your connection effectively looks like this, transferring data between you and your destination via your ISP:
With a VPN in place, your encrypted data travels via the VPN servers, effectively blocking your computer’s identity.
“When it reaches the target, it seems that the data has originated from these servers, instead of your own computer.” – Julie Cole
What Are the Pros and Cons of Using a VPN?
We’ve covered many of the pros already:
- Your traffic is encrypted
- Your IP address is hidden
- VPN can cut through regional censorship (helping gain access to regional-specific services like Netflix and Spotify for example)
In terms of the downsides, there really aren’t many, besides:
- Connection speed (routing through an additional layer of servers, perhaps on the other side of the world, could cause your connection to slow)
Taking connection speed into account should be one of the major considerations when choosing a VPN service.
How to Find the Best VPN For Your Needs
Visit VPNPro and you’ll find great resources for internet security in general, but specifically you’ll find all major VPN services tested and ranked depending on your use cases. Doing your research before committing to a VPN is really important, and the VPNPro team do all the heavy lifting for you.
The VPNPro blog is full of interesting articles about all things cyber-security, their reviews and comparisons are invaluable, the knowledge base is extensive, and you’ll especially benefit from the rankings: take a look at their Top 10 best VPN services and you’ll find links to all the best VPN services you should check out. The rankings take into account:
- Best VPN Overall
- Best VPN for Torrenting
- Best VPN for Android
- Best VPN for Kodi
- Best VPN for Mac
- Best VPN for Windows
- Best VPN for Netflix
I’m sure you identify with one of those motives! For example, if we think back to our developer who regularly works on public WiFi, their priority would likely be the ranking which pinpoints either working on a Mac or Windows platform. In these case VPNPro prioritizes:
- VPN security
- Performance
- Entertainment (effectiveness against geo-blocking, torrenting capabilities)
- Reliability against firewalls and censorship
- Ease of use and customer support
- Price
Getting access to BBC iPlayer isn’t highest on the priority list here, but being able to connect quickly and securely definitely is. Personally I use ExpressVPN, one of the pricier services available, but one which is rated very highly for all the uses mentioned above.
Personal internet security is something I didn’t give much thought to until a few years ago, but I’m glad that, since then, I’ve made a habit of protecting myself online. I highly recommend you do the same!